
User data and intellectual property in the IT industry have traditionally been protected behind a layer of perimeter security strategies. However, the global movement of development environments to hybrid cloud-based architectures has proven perimeter security measures to be inadequate. Increasingly IT companies are shifting to zero-trust network security measures with the globally recognized motto of "Never trust, always verify".
The Zero Trust Network Architecture (ZTNA) is moving approaches of all industries including finance, military, and healthcare cybersecurity from static network-based perimeters to focusing on the functioning entities of the network. Enterprise infrastructure and workflows are governed by zero-trust principles that are highly reliable and more often than not, impenetrable.
In this article, we will talk about zero-trust architecture and the principles governing the various approaches arising from this type of cybersecurity architecture.
What is Zero Trust Architecture?
Zero trust represents an evolving collection of cybersecurity concepts that focus on defenses away from rigid, network-based perimeters and towards users, assets, and resources. The industrial and enterprise infrastructure and workflows are planned using zero-trust concepts in a zero-trust architecture (ZTA).
Zero trust presupposes that there is no implicit trust given to assets or user accounts based only on their geographic or network location, for example, local area networks as opposed to the internet. The other supposition is based on the type of ownership of the asset, for example, corporate or private ownership. Before a session with an enterprise resource is established, authentication and authorization on the part of both the subject and the device are separate tasks carried out.
How Does Zero Trust Work?
A zero-trust architecture was created by John Kindervag in 2010 while a principal analyst at Forrester Research. It is a wide framework that offers efficient protection of a company's most important assets. It operates under the presumption that every connection and endpoint poses a threat. Even for those connections that have already gained inner access, the framework provides protection from these risks, whether they are internal or external.
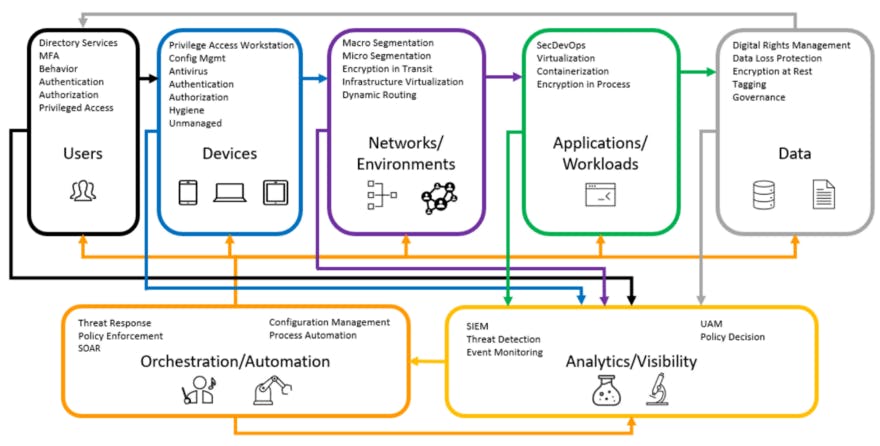
Source: Hackernoon
Put simply, a zero-trust network works by:
-Logging and inspecting all corporate network traffic
-Limiting and controlling the stakeholders who can access the network
-Verifying and making sure that all the network resources are legitimate and would not lead to a breach
The zero-trust security approach makes sure that resources and data are by default unreachable. Least-privilege access, which restricts user access to them to certain situations, is only permitted under certain conditions. When a user connects to an application or piece of software that accesses a data set via an application programming interface (API), a zero-trust security model verifies and authorizes each connection.
Principles of Zero Trust
There are certain principles of zero trust that are primarily concerned with minimizing the number of security breaches. However, the overarching principle defines an approach that always assumes that the request for entry into a network is a breach and verifies the access request. Following are some other important principles that define zero trust:
1)No Trust By Default: The zero trust security model is an approach to IT security that assumes that no network or device can be trusted by default. This is in contrast to the traditional security model, which assumes that networks and devices within the organization's perimeter are safe.
There are several reasons why no network should be automatically viewed as secure in zero-trust architecture. First, the traditional security model is no longer effective in today's threat landscape. With the rise of cloud computing and remote work, it is much easier for attackers to gain access to an organization's network. Second, the traditional security model is based on the assumption that attackers will only come from outside the organization. However, attackers can also come from within the organization, such as disgruntled employees or contractors.
2)Least Privilege: As per the principle of least privilege, or PoLP, users should only be allowed the access necessary to carry out their job duties. This idea is a crucial part of zero trust security, a method of security that operates under the presumption that no user or device can ever be completely trusted.
When PoLP is used with zero trust, users are only given access to the resources they require and only when those resources are required. This makes it more challenging for attackers to exploit vulnerabilities and helps to prevent unauthorized access to sensitive data and systems.
3)Always Assume a Breach: This principle instructs organizations to always assume that their networks and systems have already been intruded upon. Zero trust is therefore unlike the traditional security model, wherein networks are said to be secure unless proven otherwise. By assuming that a breach has already occurred, organizations can focus on preventing attackers from gaining access to sensitive data or systems.
An important aspect of this principle is micro-segmentation which divides a network into small, isolated segments. This makes it more challenging for attackers to move laterally once they have breached a network, and it also facilitates seamless containment of breaches.
4)Endpoint Protection: The zero trust principle known as endpoint protection shields endpoints, such as laptops, desktop computers, and mobile devices, against threats like malware and ransomware. Endpoint protection is a crucial part of the overall security strategy in the context of zero-trust architecture.
Endpoint protection solutions come in a variety of forms, and the optimal one for your business will rely on its particular requirements. The kinds of endpoints you need to protect, the kinds of threats to look out for, and the budget for security are some of the things to take into account when selecting an endpoint protection solution.
5)Monitor and Remediate: Zero-trust architecture refers to the process of continuously monitoring the system or network for threats and vulnerabilities, followed by applying mitigation strategies. To keep an eye out for threats and vulnerabilities, a variety of tools and procedures can be used. Among the most typical are:
- Monitoring network traffic entails keeping an eye out for any indications of malicious behavior, such as odd patterns or traffic coming from known bad IP addresses.
- Endpoint security entails the use of endpoint security tools to check devices for malware and other risks.
- User Behavior Analytics (UBA) technologies are used to track user behavior for indications of harmful activities, such as atypical login attempts or access to private information.
6)Risk Management: Any organization looking to move to a zero-trust architecture can leverage risk management helping them identify, assess, and mitigate risks to an organization's assets. Once the potential threats to the organization's assets are identified, the likelihood and possible impact of these threats is calculated.
As threats and vulnerabilities to an organization's network are continuously identified, risk management is an ongoing process for future-proofing an enterprise. Additionally, if this task can somehow be automated, crucial IT resources can be freed up to focus on other more knowledge-intensive tasks and requirements.
ALSO READ: 10 Strategic Tech Investments for CIOs in 2023
Zero Trust is an Enterprise Security Need Today
Enterprises need zero trust architecture because the traditional security perimeter is no longer effective in today's threat landscape. With the rise of cloud computing and remote work, it is much easier for attackers to gain access to an organization's network. If you are an enterprise that is looking for a more secure and effective way to protect your data and systems, then you should consider availing the Application Security Services of Daffodil Software.



