Today, the enterprise IT sector is affected by, and taking advantage of various new technologies and models, derived and developed in consumer space. This trend, called ‘Consumerization’ is impacting the enterprise-wide in a number of ways, which includes the usage of instant messaging for business.
With instant messaging apps having massive mobile messaging traffic, it has turned out to be a preferred platform for team chat, file sharing, and other interoffice communications.
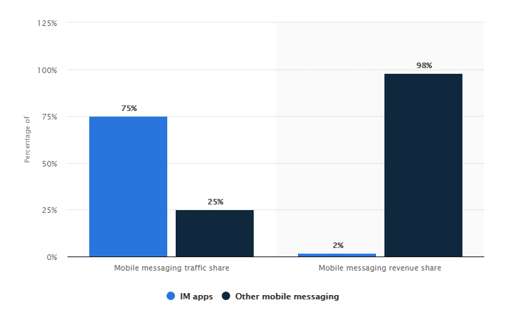 Instant messaging app share of mobile messaging traffic worldwide in 2018
Instant messaging app share of mobile messaging traffic worldwide in 2018
However, in the process of adopting an instant messaging program for business, there are some security loopholes that needs to be addressed and fixed. Reason being, exchanging data over untrusted IM apps on mobile can hamper sensitive business data. Therefore it is important to create a list of security essentials that ensures integrity and confidentiality of data.
Enterprise Instant Messaging: Key Challenges
- Volume of data shared through mobile instant apps is quite large. Sharing of data over MIM puts confidentiality to risk, increasing likelihood of data leakage. This may include open wireless network, malware attack, device loss etc.
- Absence of security compliances to evaluate office messengers, before they are permitted to be used at enterprise level.
Practical Solutions:
- Authentication
- At basic level, authentication ensures ownership of the account. In most of the IM solutions or other apps, this is done via Password Authentication Protocol, wherein a username and password is used to validate a user’s credential on server.
- Some applications use device to authenticate the user. Examples of such authentication is built-in messengers for specific OS (example: iMessage for iOS devices). Once the user unlocks the iPhone or iPad, the device validates the user and enable its usage. For this, a device password can be enforced.
For device authentication, it is recommended not to opt for user identities, i.e. biometric authentication. This may create issues in imposing any change in the device security, in case the user is not available. - Another way to secure instant messaging system for business is to use hardware-based encryption for stored credentials. This can be done using GSM authentication, wherein the PAP authentication uses the stored credentials to validate the user. This is called certificate-based authentication, wherein a digital certificate is used to access a resource, network, or application.
Takeaway:
User and device based authentication, when practiced individually have a few pitfalls. While passwords are vulnerable, an alphanumeric passcode with good length can help to offer the much needed security. Also, using certificate-based auth ensures that before the IM is accessed by the user, a certificate validates the device to access the application. Therefore, a combination of user and device authentication should be used to bypass any access vulnerability.
- Encryption
The data exchanged through instant messaging platforms, text or file-based needs to be encrypted, for safeguarding it against eavesdropping. This can be achieved through various encryption models like:
- End-to-End encryption, where the messages (text or files) are encrypted with a key, which is saved on users device. The data shared can be decrypted on other device using the same key. This way, the data between two parties can be accessed by them only.
- In some of the apps, the end-to-end encryption is achieved using the Off-the-Record messaging, which is a cryptographic protocol, securing instant messaging conversations. This encryption level ensures that no government, network provider, or even the IM service provider can access the messages.
- Another option to keep your instant messaging apps for business secure is to opt for PIN encryption. This will save the data to be exchanged over networks and therefore, from the eavesdropping. Such type of encryption was seen back in Blackberry messenger (BBM), wherein users share their PIN to exchange messages. While the no internet concept works in favor of security, the PIN encryption requires same mobile devices, availability of alphanumeric pin etc.
Takeaway:
With encryption, IM applications can offer advanced security levels. One of the finest security options that can be integrated to an interoffice messaging app is end-to-end encryption as it will ensure integrity maintenance of text as well as file level data (as we have in Facebook Messenger and Whatsapp).
- Server Location
Encrypting messages help to retain their confidentiality. However, in this process, the location of server matters and in this respect, there are some approaches and following them makes sense for a better enterprise instant messaging system.
Takeaway:
Alongside authentication and encryption, it is important for organizations to deploy corporate IM servers that integrates with the corporate directory service infrastructure (LDAP).
Need Custom Instant Messenger for Business? We can Help
There are N number of messaging apps in the market. While some are good at authentication, some at encryption, it is important to have one that has a rare and strong combination of the security factors shared above. For a custom instant messaging application development for enterprise, share your requirements with us.