
The DevOps paradigm has predominantly been focused on delivering high-quality software products to customers faster through shortened release cycles. Ensuring continuous security for these products is an essential aspect that is implemented by the DevSecOps domain. But when it comes to security in the product's design and architecture you need a more dedicated system such as that offered by Threat Modeling.
For optimal DevOps security, threat modeling could be adopted as part of the development lifecycle. Threat modeling is a great way to enhance the effectiveness of the risk management process of the DevOps workflow. It helps with identifying risks much faster and acting on them swiftly before the code in development encounters major production errors.
In this article, we will discuss how threat modeling can be intelligently integrated into the DevOps workflow, more specifically the DevSecOps domain. We will begin by introducing threat modeling.
What is Threat Modeling and Why is it Important for DevOps?
Threat modeling is the process of identifying your software or system's vulnerable points of entry for malicious attacks and then mitigating the associated risks. These risks are usually detected during the design and architecture phase of the software product.
A description in the form of a flowchart or diagram is then formulated to help visualize the potential threat to the system or software. Threat modeling for DevOps requires a precise and systematic approach for detecting threats and risks in time and performing fast remediation.
A rigorous or structured approach to threat modeling is needed when it comes to developing and delivering software applications using the DevOps approach. When performing threat modeling on software applications, it is crucial to keep the definition above in mind. It can be all too easy to get caught up in too many formalities when performing threat modeling in this context, such as particular categorizations, diagram types, and tools - sometimes at the expense of maintaining focus on what is crucial, which is recognizing and visualizing the possibility that something negative or harmful could transpire.
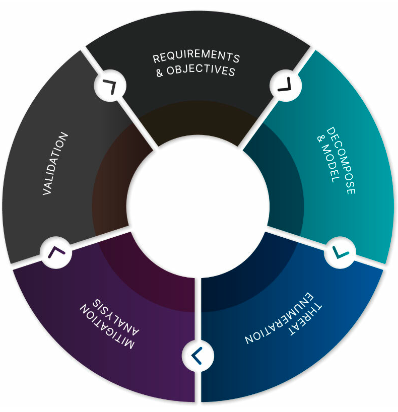
Image: Threat Modeling Methodology
The following explains step-by-step the entire threat modeling methodology:
1) Requirements and Objectives:
In this initial phase, the business environment where the software application functions are analyzed to get a detailed account of the major use cases of its implementation. This is followed by identifying its business criticality and its potential for risk. This phase ends with the realization of the purpose behind the construction of the threat model.
2) Decompose the Application:
At this stage, the application is broken down into manageable components to get a detailed analysis of its design and architecture. This decomposition helps create a model for visualizing potential threats to the application. The most crucial architectural segments, system framework, and networks are diagrammed into the model to understand data flows and trust boundaries measuring the level of the system's trust.
3) STRIDE Threat List:
STRIDE stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege, and enumerates all the potential threats into well-defined categories. This mnemonic device was created by Microsoft to help developers and testers responsible for an application understand the motives of potential attackers.
4) Formulating Countermeasures:
Once the threats have been visualized diagrammatically, the next step is to develop measures to mitigate the risks identified. These countermeasures also need to be documented for easy referencing at a later stage. Technical as well as policy risk mitigation measures are created and then documented rigorously.
5) Review:
All the security architecture, control, and design changes have been incorporated following the threat modeling and are reviewed carefully. This is to identify any threats that have not been mitigated appropriately with the most fitting countermeasures so that there are no long-term risks to the organization or its product.
Integrating Threat Modeling with DevSecOps
As DevSecOps involves the inclusion of security in each step of the DevOps-driven software development lifecycle, threat modeling fits into the picture like a puzzle piece. As threat modeling is meant as a collaborative activity in the same vein as several stages of the DevOps lifecycle involve communication between multiple teams, both these practices work well with each other. Once a set of best practices have been formulated and the associated challenges have been addressed, threat modeling can be effectively integrated into DevOps leading to the following practices:
1) STRIDE Analysis:
A good rule of thumb for developing threat modeling strategies for DevOps is to compare the threats that arise from an initial analysis of the application in its business environment with the STRIDE framework. It is always useful to be able to predict all the possibilities of things going wrong when the code breaks or the application doesn't run in a different environment. Other issues have to do with access and identity control, spoof attacks, data leaks, and so on, which are highly detrimental to a software product's development.
2) Account for Business Risk:
The threat modeling process coupled with the DevOps approach does away with silos and brings developers closer to the business teams. When an amalgamated view of the entire risk mitigation workflow including the business aspect becomes available, you have the scope of weighing the business risks of the threats that have been detected. Ultimately, both the development and business or operations side of software development become free from debilitating risks.
3) Stronger Communication Loops:
The main purpose of implementing the DevOps approach is to shorten the communication pathways between the development and business teams and in turn tighten the deployment cycles. Threat modeling helps to further improve these networks to gain better control and visibility over the entire software development workflow so that a more tangible and readily executable plan can be worked out.
4) Automation Tooling:
There is an unlimited arsenal of automation tools that power the DevOps paradigm and several of these can help automate aspects of the threat modeling approach. Integrating the DevOps toolchain with that threat modeling can achieve software development targets faster while also ensuring quality and robustness.
ALSO READ: What is Threat Modeling and its role in developing secure systems?
Combine DevOps Automation with Threat Modeling
By identifying potential vulnerabilities and risks, teams can proactively implement security measures to prevent attacks and protect sensitive data. DevOps teams should prioritize threat modeling early in the development cycle and continuously review and update it throughout the software development life cycle.
By adopting a proactive and comprehensive approach to threat modeling, you can ensure the security and resilience of your applications and infrastructure. To find out how you can leverage Daffodil's DevOps expertise for the same, book a free consultation with us today.



