As of 2024, the Office for Civil Rights (OCR) has settled 142 cases of HIPAA violations, resulting in various covered entities facing over $142 million in penalties for non-compliance. These penalties, although significant, represent only a fraction of the consequences for violating HIPAA.
Moreover, the fallout from such breaches goes beyond financial penalties. Companies that experience a HIPAA violation are publicly listed on the OCR's "Wall of Shame," which provides details about the infraction, the date of occurrence, the penalty amount, and the number of individuals affected.
That's a lot to handle, isn't it? As per our healthcare IT experts, the best strategy to sidestep these consequences is to prioritize and strengthen your business's adherence to HIPAA regulations.
So, if you're unsure whether your organization is at risk of penalties, keep reading this article to explore what HIPAA compliance entails, the violations to avoid, and the essential measures for robust adherence to these regulations.
A Brief Overview of HIPAA Compliance
HIPAA, also known as the Health Insurance Portability and Accountability Act, holds a significant place in the history of healthcare legislation in the United States.
Passed into law during President Bill Clinton's tenure in 1996, HIPAA isn't just for healthcare providers. It applies to various players in the healthcare field, including health plans, clearinghouses, and those who work closely with these entities.
But why did policymakers feel the need to introduce HIPAA? There were two primary reasons:
Firstly, HIPAA aimed to crack down on healthcare fraud by setting rules to ensure the proper handling and disclosure of protected health information (PHI). These rules changed how HCOs handled and shared patient data to prevent misuse.
Secondly, to ensure that people wouldn't lose their health insurance coverage when they changed jobs. Before HIPAA, this was a real concern, leaving individuals in limbo regarding their healthcare expenses during job transitions.
Monitoring HIPAA compliance is the responsibility of the Department of Health and Human Services (HHS), while enforcement actions are managed by the Office for Civil Rights (OCR). The OCR plays a crucial role in upholding HIPAA standards by providing regular guidance on emerging healthcare issues and investigating common violations of HIPAA regulations. For providers uncertain about texting patients under HIPAA, this guide to HIPAA-compliant texting outlines the risks of non-compliant messaging and offers practical safeguards for secure communication.
Who is Subject to HIPAA?
In order to protect data privacy and prevent any potential repercussions, it is essential to first determine who falls under the umbrella of HIPAA compliance. Generally, there are two main groups of organizations that must adhere to HIPAA regulations:
1. Covered Entities: According to HIPAA, a covered entity refers to any organization that electronically collects, generates, or shares protected health information (PHI). These entities can be classified into three categories:
- Healthcare Providers: Including doctors, dentists, clinics, pharmacies, nursing homes, and any other healthcare facility or professional collecting PHI, must adhere to HIPAA standards.
- Healthcare Plans: Such as health insurance companies, HMOs, and government-funded programs like Medicare & Medicaid, fall under the covered entity category.
- Healthcare Clearinghouses: Organizations converting PHI data into a standard format for electronic transmission are also considered covered entities.
2. Business Associates: Under HIPAA, a business associate is described as any entity that comes into contact with PHI while performing tasks contracted by a covered entity. The range of services that may involve handling, transmitting, or processing PHI is extensive, leading to numerous examples of business associates.
Examples of business associates include:
- Entities responsible for handling and processing healthcare billing information.
- Organizations managing administrative tasks for healthcare practices.
- External hospital consultants conducting evaluations.
- Platforms facilitating the digital storage and management of patient health records, e.g. EHR systems.
- Administrators assisting with claims processing for healthcare plans.
- Firms specializing in secure disposal of sensitive healthcare documents.
- Entities offering storage solutions for both physical and digital healthcare data.
- Professionals offering legal and financial services to healthcare entities.
While business associates may not directly interact with patients, they must sign a business associate agreement (BAA) to uphold HIPAA regulations regarding PHI protection.
3. Hybrid Entities: A hybrid entity typically engages in both HIPAA-covered and non-covered activities within its business operations.
For instance, banks or financial institutions that provide health savings accounts (HSAs) may qualify as hybrid entities, with only the healthcare-related division subject to HIPAA compliance.
Other instances of hybrid entities include-
- Educational institutions with medical facilities, where only healthcare operations adhere to HIPAA.
- Factories with on-site medical services,
- Stores with medical clinics.
Hybrid entities must ensure strict segregation between their healthcare component and non-covered segments to prevent the disclosure of PHI to non-compliant areas within the organization.
4. Researchers: HIPAA regulations permit covered entities to share PHI with researchers when patients have given consent for research use.
- No business associate agreement is required in these instances.
- Instead, a data use agreement must be established between the covered entity and the researcher before disclosing PHI.
- The data use agreement ensures strict adherence to HIPAA compliance guidelines for the limited data set, providing assurance of compliance.
Who is Not Subject to HIPAA?
Numerous individuals and businesses must adhere to HIPAA regulations, but many others are exempt. Despite this, there are instances where health information may still be accessible to these exempt entities. Here are some examples of those not bound by HIPAA:
- Gyms and fitness centers
- Mobile apps related to health and fitness
- Most law enforcement agencies
- Educational institutions and school districts
- State entities such as child welfare departments
- Providers of workers' compensation insurance
Additional examples of such entities can be found in the HHS Guidance Materials for Consumers.
Key HIPAA Rules You Need to Follow
HIPAA regulations consist of several rules that have been enacted over the past two decades since its inception in 1996. But here’s the major three rules that you must follow:
1) Privacy Rule
The HIPAA privacy rule sets the guidelines for when someone can share or use protected health information (PHI). While privacy is important, there are times when this rule applies. Those who need to follow this rule must stick to certain guidelines.
These guidelines cover:
- Who needs to follow HIPAA rules
- What counts as protected health information
- How organizations can share and use this information
- When it's okay to share or use this information
- Patients' rights regarding their health information
Covered entities must respond to requests for access or disclosure within 30 days.
2) Security Rule
The HIPAA Security Rule lays down the basic requirements for keeping electronic health information (ePHI) safe. Even if someone has the ability to access this information electronically, they must meet these standards.
Here's what the HIPAA Security Rule covers:
- Which organizations need to follow it (covered entities)
- Ways to create policies and procedures to meet HIPAA standards
- What healthcare information is protected by this rule
Simply put, anyone who is part of a Business Associate (BA) or Covered Entity (CE) and can view, change, make, or send electronic health information must adhere to these standards. These standards include using NIST-standard encryption if the information leaves the company's secure network.
Besides technical safeguards, the Security Rule also involves physical safeguards. For instance, in public areas, screens are positioned so that they can't be easily viewed. Access to certain parts of the company's network is restricted to specific areas.
3) Breach Notification Rule
This rule dictates the procedures that covered entities and business associates must follow in the event of a data breach involving PHI or ePHI. It outlines various reporting requirements depending on the size and scope of the breach. Regardless of size, all breaches must be reported to the HHS OCR, with specific reporting protocols varying based on the breach type.
What do HIPAA Violations Entail?
Compliance with HIPAA means following the rules laid out in the Privacy, Security, and Breach Notification Regulations. If an organization fails to adhere to these standards, they are deemed to violate HIPAA.
Violations can include:
- Unlawfully exposing electronic Protected Health Information (ePHI) to unauthorized parties, whether intentionally or accidentally.
- Failing to implement proper security measures as outlined by the HIPAA Security Rule.
- Lacking adequate administrative or training protocols that meet requirements.
- Neglecting to notify affected parties and relevant authorities following data breaches.
- Being unwilling to update, upgrade, or address existing compliance gaps.
Some Common examples of violations include:
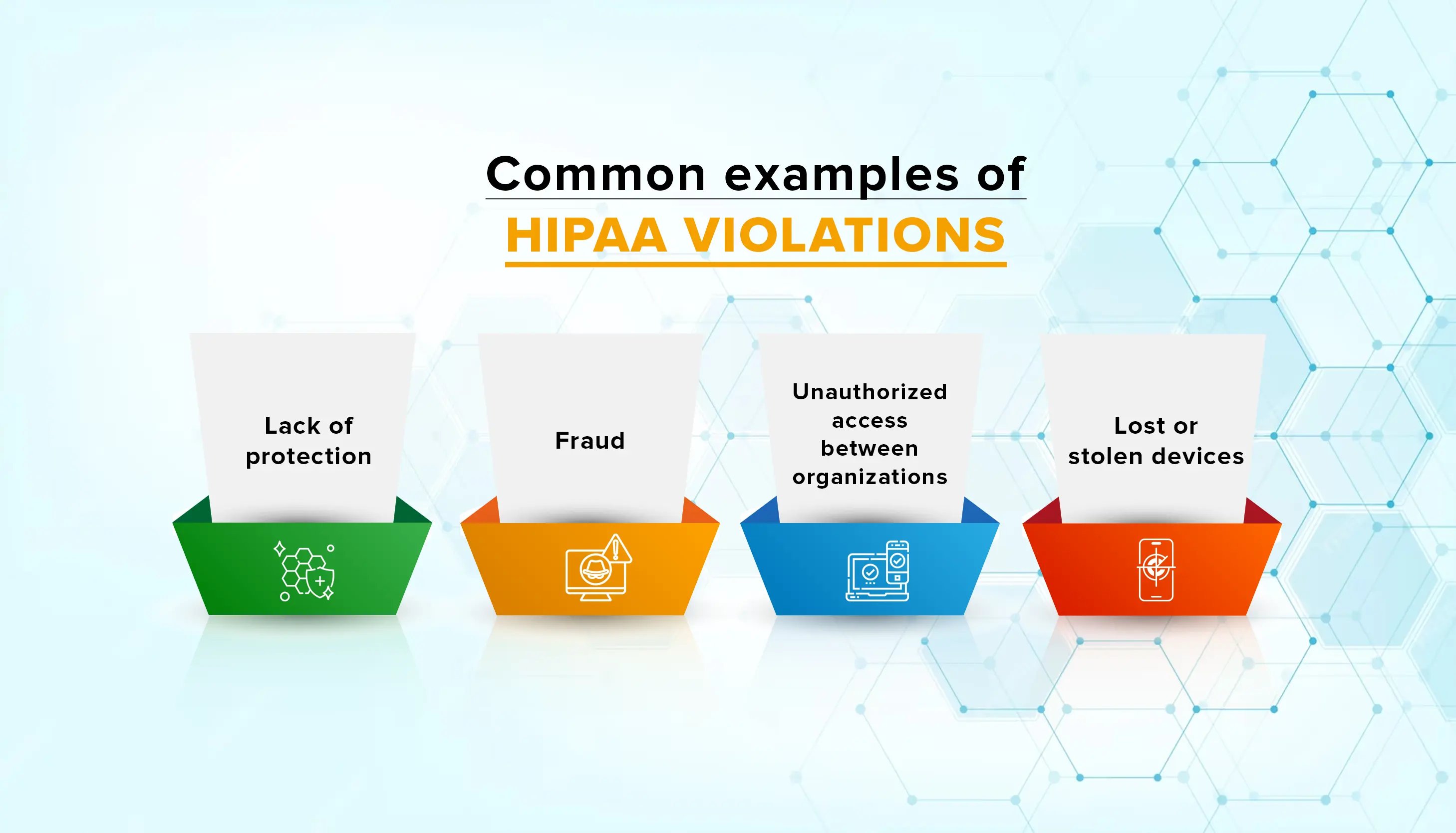
Lack of protection: Many organizations may not fully understand the security measures required by the Security Rule or may work with third-party providers who claim compliance but fall short.
Fraud: This occurs when individuals steal ePHI for personal gain. While rare, incidents involving hackers or insider operations are becoming more common as healthcare facilities adopt cloud technology and rely on unproven service providers.
Unauthorized access between organizations: Whether through sharing data with unauthorized individuals or using unencrypted devices or email, it's easy for untrained staff to mishandle ePHI. Accidental disclosure of PHI is the most common violation, leading to lower-end penalties.
Lost or stolen devices: With the increasing use of mobile devices like laptops, tablets, and smartphones in healthcare settings, the risk of these devices falling into the wrong hands has grown.
But What Happens if You Inadvertently Breach HIPAA Regulations?
Not all instances of violating HIPAA security stem from deliberate negligence. Given the complexity of its requirements and the various potential vulnerabilities, it's understandable if an organization unintentionally overlooks HIPAA compliance standards. For instance, healthcare professionals might exchange electronic Protected Health Information (ePHI) to facilitate urgent medical care. In such scenarios, secure systems can help mitigate the potential repercussions of disclosure without impeding healthcare workers' ability to respond promptly and decisively.
Primarily, there are several ways to inadvertently breach HIPAA:
- Intentional circumvention: Such as when a medical professional shares information through non-compliant channels to expedite urgent treatment.
- Accidental exposure: Unintended disclosure of information.
- Intentional disclosure: Resulting from theft or hacking, often originating from an individual within the organization.
If you or your healthcare entity accidentally violate HIPAA regulations, it's crucial to report it within 60 days of discovering the breach. Timely notification can help minimize the fallout from data breaches.
Following an inadvertent violation, fulfill any necessary requirements imposed by HIPAA for compliance (reporting, notifications, etc.). Depending on the circumstances, especially if data access was unintentional, the actual compliance obligations may be minimal.
If the inadvertent violation falls within any of the potential scenarios mentioned above (occurred in good faith internally, between authorized personnel, or with evidence that the data won't be retained outside the organization), the concern over the violation may be lessened.
Identifying a violation as accidental carries significant weight in terms of penalties. Fines for violations can vary from $100 to $50,000 per incident (per compromised record), depending on the type of data, the origin of the vulnerability, and whether the breach was accidental or due to deliberate negligence.
HIPAA Violation: Tiers and Penalties
HIPAA categorizes violations into two groups: civil and criminal.
Civil violations are instances of noncompliance that occur accidentally or without malicious intent. These may involve negligence or lack of awareness. Penalties for civil violations tend to be less severe:
- For individuals unaware of violations, the fine is $100 per incident.
- For those with reasonable cause but without neglect, the fine is a minimum of $1,000.
- Willful neglect incurs a minimum fine of $10,000 per incident.
- If willful neglect continues without immediate rectification, the minimum fine is $50,000 per violation.
Criminal violations involve actions committed with malicious intent, such as theft, fraud, or profiteering. Penalties for criminal violations include:
- Knowingly obtaining or disclosing ePHI can result in a fine of up to $50,000 and 1 year in jail.
- Committing fraud as part of the violation can lead to a fine of up to $100,000 and 5 years in jail.
- Engaging in violations with the intent to profit from them can result in a fine of up to $250,000 and up to 10 years in jail.
- Numerous and repeated violations can cost organizations millions of dollars annually.
Real-World Examples of HIPAA Violations
- In 2013, CVS Pharmacy agreed to pay $2.25 million to settle HIPAA violations related to the improper disposal of prescription bottles and labels containing patient information. The bottles and labels were disposed of in open dumpsters accessible to the public.
- A healthcare facility disposes of patient records in a public dumpster without shredding them first. In 2016, the Feinstein Institute for Medical Research agreed to pay $3.9 million to settle charges related to the improper disposal of research participants' medical records.
- In 2018, the University of Texas MD Anderson Cancer Center was fined $4.3 million for three separate HIPAA violations. These violations included the unauthorized disclosure of ePHI by employees and the lack of encryption on electronic devices containing patient information.
Achieve HIPAA Compliance with this Step-by-Step Checklist
Given the sensitive nature of data handled by many organizations, especially in the healthcare sector, adherence to HIPAA standards is crucial. We have prepared a self-checklist for HCOs to spot areas where they might not be following the rules and fix them before they get audited by the Department of Health and Human Services (HHS). Here's a checklist you can use to do your own HIPAA compliance check:
.png?width=1424&height=1533&name=Frame%201%20(2).png)
- Designate a HIPAA Compliance Officer to oversee your compliance efforts, ensuring all security measures are in place.
- Create an inventory of patient data, categorizing it based on sensitivity to prioritize protection efforts.
- Provide training to IT personnel on HIPAA requirements, emphasizing the importance of data security.
- Develop clear policies and procedures for handling patient data across all IT systems and environments.
- Implement strong access controls, such as password protection and screen locks, on all devices accessing patient records.
- Secure physical and electronic records, limiting access to authorized personnel through user authentication.
- Employ encryption tools to protect patient data stored on devices and during transmission, safeguarding it from unauthorized access.
- Install web filters and email encryption tools to prevent unauthorized access and protect against phishing attacks.
- Establish secure disposal methods for physical and electronic records, ensuring data is irretrievable after disposal.
- Develop a protocol for responding to security incidents, including steps for investigation, containment, and notification.
- Continuously review access logs and audit trails to detect and respond to any suspicious activity or unauthorized access attempts.
- Keep detailed records of user activities and changes made to patient data, facilitating accountability and compliance.
- Establish regular backup schedules and off-site storage solutions to ensure data availability and integrity in case of system failures or disasters.
- Develop a comprehensive plan for restoring IT systems and operations in the event of emergencies, minimizing downtime and data loss.
Empowering Healthcare Organizations with HIPAA-Compliant Solutions
HIPAA provides flexibility for organizations to choose the best technology and procedures to protect sensitive health information. Keeping electronic patient health data secure is tough but crucial for complying with HIPAA. With increasing cyber threats, organizations and IT departments must find ways to better manage access, protect data, and reduce the risk of unauthorized use.
Daffodil builds secure and HIPAA-compliant solutions for covered entities and their business associates, offering granular access controls and top-tier encryption to safeguard protected health information. From Electronic Health Record (EHR) Systems and Compliance Management Software to Mobile Health (mHealth) and Telemedicine Platforms, our expertise spans the spectrum. We're dedicated to crafting tailored solutions that empower organizations to govern, protect, and control sensitive content in full compliance with HIPAA and other data privacy regulations.
Schedule a no-obligation call with our health IT experts to discover how Daffodil can support your journey toward HIPAA compliance.






