
The new norm of practicing DevOps has recorded success in streamlining and improving the deployment cycle. With benefits like automation, faster-time-of market & incident responses, DevOps has had a positive impact on the overall delivery of an application.
However, as the applications become large in scope, and involve people, tools, & services in great numbers, it adds new complexities for managing, securing, and troubleshooting applications. To work around these challenges, it is important to streamline and secure the DevOps pipeline.
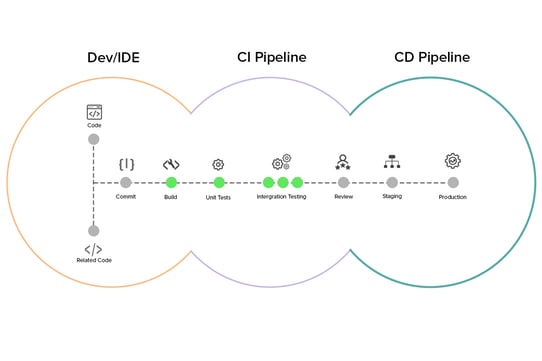
A DevOps pipeline is a set of automated tools and processes that takes care of development and operations tasks to ensure that an application is timely built and deployed to a production environment. This pipeline or the DevOps workflow varies by organization, the scope of a project, or the implementation of processes. Containers, orchestration services, automation testing, cloud, and other services add up to better management and performance of a DevOps pipeline.
There is no standard to create and maintain a DevOps pipeline. And when something lacks standardization, it results in security, maintenance, and compliance issues, which surely need to be addressed. With this, we have a real problem in the spotlight: how to secure a DevOps pipeline?
In the latter segment of this blog post, we will be discussing 5 key practices (directly shared from our DevSecOps engineers’ desk) that would guide your way to secure and streamline a DevOps pipeline.
DevSecOps to Secure a DevOps Pipeline
DevSecOps is a practice in application security that involves introducing security in the earlier stage of a software development cycle. The practice ensures that the development and operations team takes accountability for security action and implementations in an SDLC.
To assure that the DevOps CI/CD workflow follows security compliances and adheres to the performance standards, the following practices can be incorporated by the DevSecOps team:
- Regular Container Scanning
Containers are black boxes. It is hard to figure out what’s going on inside them. As the number of container images, versions, and builds increases, it is important to regularly scan the containers to identify vulnerable configurations, malware infections, compliance breaches, etc.
Container scanning is the process of comparing the contents of a container image with an existing database of vulnerabilities. This is done using automation tools. If any of the libraries or dependencies within the container image are found to be vulnerable, the tools flag the container as insecure.
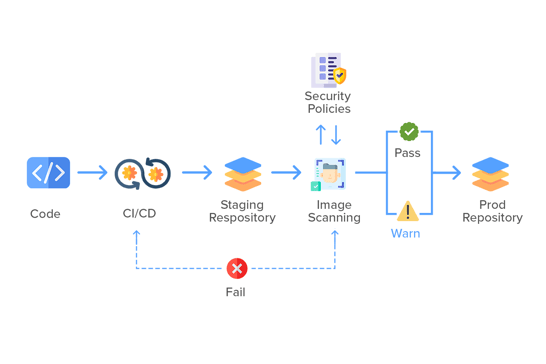
One of the prime limitations of container scanning is it doesn’t allow to detection of unknown vulnerabilities, i.e. security issues that are not publicly disclosed or made available to security analysts. So, if a container image (for example) uses a library that has a security bug but is not recorded in the vulnerability database, it may not be tracked.
Container scanning, however, is just one step towards ensuring a secure CI/CD pipeline. It can help to detect and block known vulnerabilities at the initial level and shift security left in the pipeline.
- Manage CI/CD Access Controls
Access controls are another practice to manage the security of tools and resources in a CI/CD pipeline. This prevents any kind of attack that could have an impact on the development environment.
Securing a CI/CD pipeline with access keys, passwords, and access controls ensure that it is only used by team members who specifically need it. Such practices also help to abide by the principle of least privilege and minimize the possibility of attackers having the key to a CI/CD environment.
Another approach to secure a DevOps workflow is secrets management. Secrets such as passwords or access keys should are often required in a CI/CD pipeline to integrate code, test, or deploy applications to production, etc. While for many, hard coding these secrets into CI/CD configuration files could be a way around, this certainly is not secure. Instead, a secrets manager should be there in place to store and access sensitive data on an as-needed basis during critical operations in a CI/CD cycle.
- Static Application Security Testing (SAST)
SAST is a white box testing that assesses a source code to find security vulnerabilities. This testing methodology is suitable for CI/CD security scanning because it checks the code before it is compiled.
SAST performs configuration analysis, semantic analysis, data flow analysis, control flow, and structural analysis. This includes practices such as:
- Checking configuration files of the application
- Identifies issues in class design, declaration of variables & functions
- Examines language-specific code structures for inconsistencies
- Checks data flow and validate if the input is valid before use
Static testing tools provide developers with real-time feedback as they code. This ensures that any security issue is not passed on to the next phase of the SDLC cycle. Tools that help in static testing (generally) provide a graphical representation of issues found, and best practices to work around them, without requiring deep domain-level expertise.
- Dependency Management
A dependency in software development is a piece of code, library, or functionality essential to run a different part of the code (this could simply be a specific library).
Dependency scanning is the process of finding vulnerabilities in software dependencies while developing and testing the application. Automation tools for this activity generally create a list of dependencies and check them against known vulnerabilities. This may also include using multiple versions of dependencies, which ultimately creates inconsistencies.
- Ensure Pipeline Monitoring
A DevOps cycle should be continuously monitored at the infrastructure, application, and network levels. There are several automation tools available that help in monitoring the software development cycle. There are tools and processes for monitoring networks, hardware, software, performance & health of the applications in production. In addition to these, DevOps monitoring tools also scan the network activities and components such as routers, firewalls, routers, etc., and detect security vulnerabilities across the network.
ALSO READ: A CTO's Guide to DevOps and its Services
Conclusion:
DevOps CI/CD pipelines have important information about the software delivery process. This includes system access, environment configurations, codebase, etc., which can be a help to help attackers to exploit the environment. That is why securing the CI/CD pipeline should be on the prime list of the DevSecOps team.
When securing a DevOps workflow, there are two critical aspects in consideration:
- Ensuring the security of code
- Ensuring the security of the pipeline
If automating DevOps workflow is on your business’ tech roadmap, then our DevOps services are what your business needs right now. To know how to get started with it, connect with our experts with a free, no-obligation consultation.



